Montreal IT Company
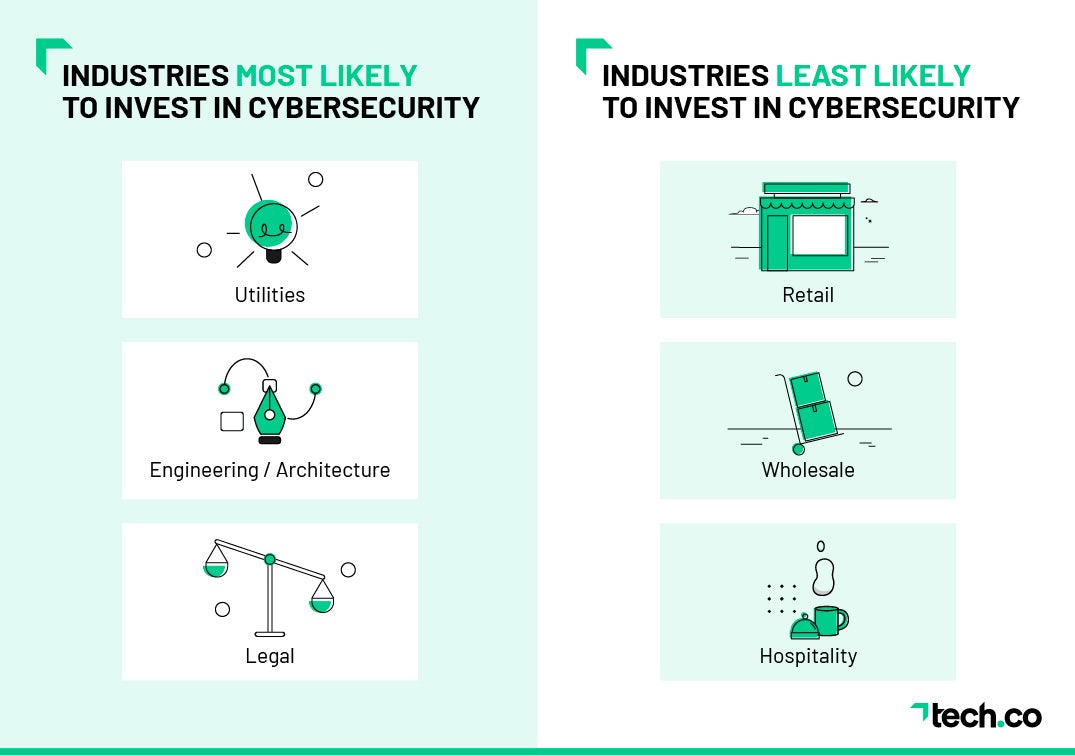
Over 70% of Small Businesses Fail to Prioritize
Cybersecurity!
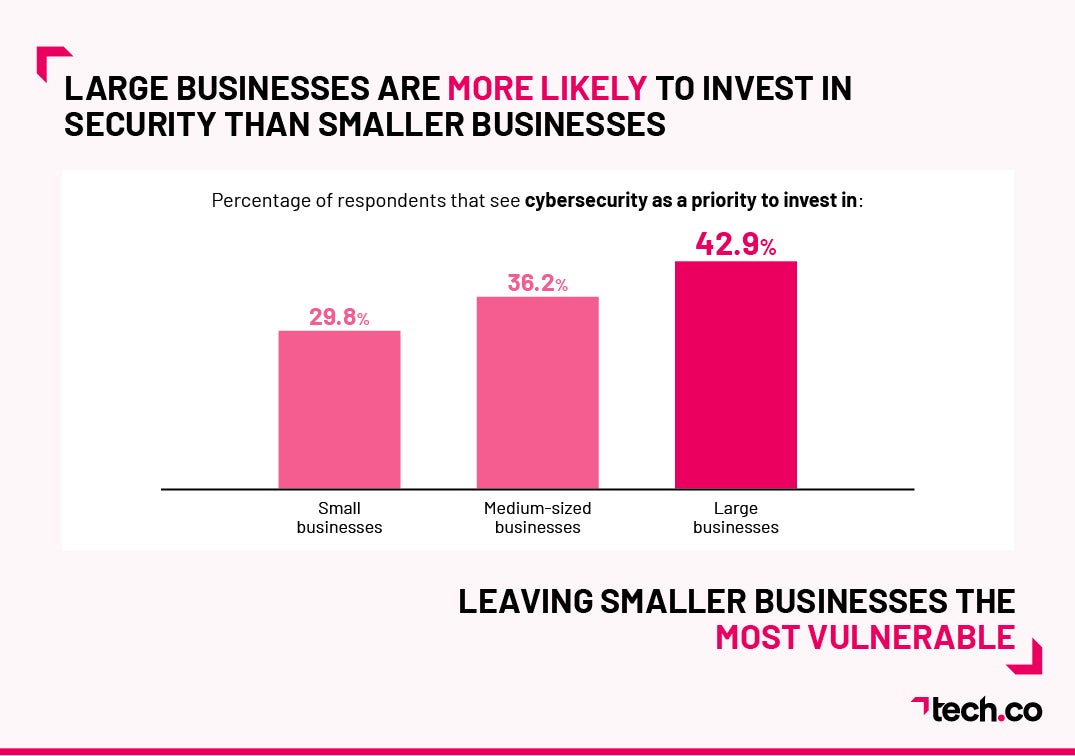
Here are the Industries Least Concerned About Cybersecurity:
CLOUD COMPUTING
*Cloud computing is expected to be a $241 billion market by 2020. Some of the most popular cloud-based platforms include OpenStack, Microsoft Azure, Google Storage, and Amazon Web services.
*It is far easier to turn up, turn down, or turn off cloud-based servers than physical servers.
Here are some Cloud advantages :
- Data Redundancy and Replication: Most cloud storage vendors keep multiple copies of your data even within a single “data center” and offer great object durability to reduce any likelihood of data loss.
- Data Tiering for Cost Savings: Many cloud storage vendors offer different storage classes / data tiers. Select based on how quickly and frequently you restore backups and how long you plan to keep your backups in storage.
- Regulatory Compliance: Keeping your backups in the same region as where the data originates may be best for regulatory compliance. Many cloud vendors offer data centers options all around the globe.
- Ransomware/Malware Protection: Ransomware is just bad. If you’re hit by ransomware or some other malware that is encrypting or destroying files, you might be happy that your cloud storage can help to protect against ransomware by offering some backup security advantages as it’s more difficult to access without proper authentication.
- Cloud Storage Can Save Costs: Cloud vendors buy a lot of storage and pass those savings onto customers.
Here are five cybersecurity tips :
1) Install antivirus software.
Installing antivirus software on every computer, regardless of size, is the first and most important step in any cybersecurity effort. Make sure you have the most recent version of your antivirus software and keep an eye out for updates.
This is especially important if you have multiple computers that aren’t always online (e.g., a local office). It should suffice if you can install something like Microsoft Defender.
2) Keep up with security announcements.
Staying current on security announcements from your computer and software providers is critical because, even if you’re doing everything correctly, there could be a new vulnerability that you’re not aware of. If you don’t check in with providers on a regular basis to ensure your software is up to date, hackers can exploit these flaws for malicious purposes such as identity theft. Small businesses must be concerned about the latest computer security trends in addition to being aware of security risks posed by their technology.
3) Turn on two-factor authentication.
Two-factor authentication is a protocol that requires you to verify your identity using two types of identification: something you know (such as a password) and something you have (like your smartphone). Logging in requires entering a special code sent to your phone via text message in addition to your username and password. While this protocol is not perfect, it is extremely useful in providing security for users who want an extra layer of protection.
4) Encrypt sensitive information
- Encrypting data is important for any company, but it is critical for local small businesses. If you encrypt your data, hackers will be unable to access it in the event of a cyber-attack.
- When sensitive data is encrypted, it is sent through an algorithm that renders it unreadable to anyone who does not have access to a special key or password. The key is what allows users (and applications) to decipher text encrypted with a specific algorithm.
5) Upkeep and monitoring of software
Because technology is constantly changing and evolving, it is critical to maintain and monitor your software to protect your data. Most software includes an update button that takes less than a minute to complete and is simple for you or your IT specialist to perform every couple of weeks.